We expect to save over $12 million in data risk reduction and operational efficiency in the first 3 years.
— Leading U.S. Teleco

Unified Data+AI Security Solution for Your Enterprise
Discover Where Your
Sensitive Data Lives
Identify shadow, regulated, and high-risk data to apply controls where it matters most and reduce exposure risk.
See a Demo
Uncover Who Has Access
to Your Sensitive Data
Get granular insights into users, roles, and permissions to enforce least-privilege data access.
See a Demo
Track How Your Sensitive
Data Moves
Leverage data maps to visualize how sensitive data moves across the enterprise & enforce governance policies.
See a Demo
Automatically Remediate
Data Risks
Right-size access entitlements, fix risky misconfigurations, and enforce policies to strengthen data security posture.
See a Demo
Minimize Redundant,
Obsolete, & Trivial Data
Automatically quarantine or delete ROT data based on age, activity & data retention policies to reduce cost and improve AI efficacy.
See a Demo
Secure AI Agents and
Copilots at Scale
Apply access controls at scale to prevent sensitive data oversharing by design.
See a Demo
Ensure Compliance With
Multiple Frameworks
Automate technical control tests to assess compliance across global regulations and emerging frameworks.
See a Demo
Quickly Respond to Data
Breaches
Analyze exposed identities, regulatory obligations, financial penalties and notify data owners to reduce breach impact.
See a Demo
6 Data Security Posture Management (DSPM) Use Cases
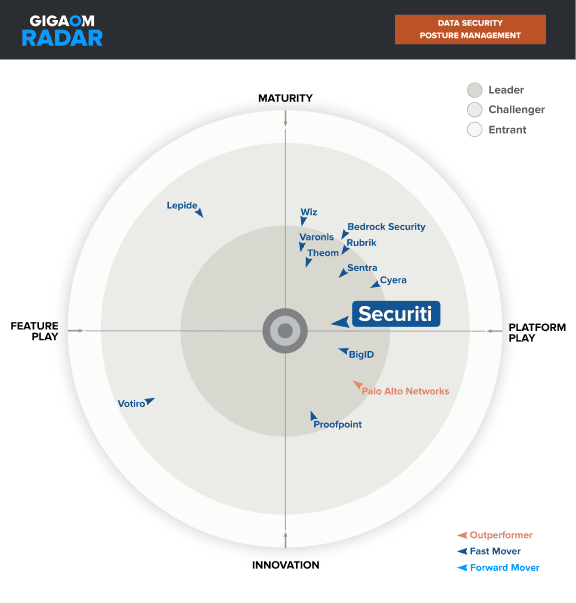
Securiti Ranks #1 in DSPM
Break Silos of Data
Intelligence & Controls
Silos for each Cloud and Silos for Security, Privacy, Governance, Compliance

Ready to see #1 DSPM in Action
Request a demoCopyright © 2025 Securiti · Sitemap · XML Sitemap