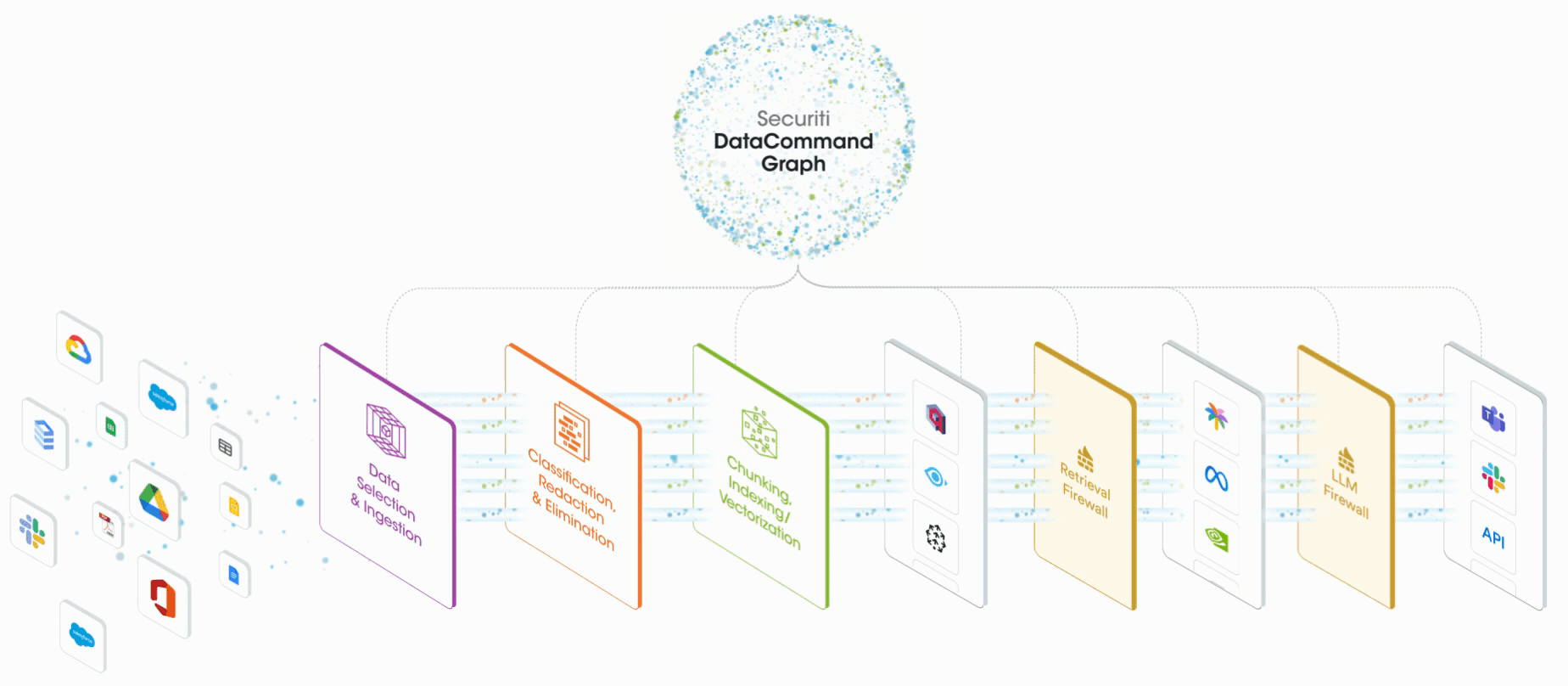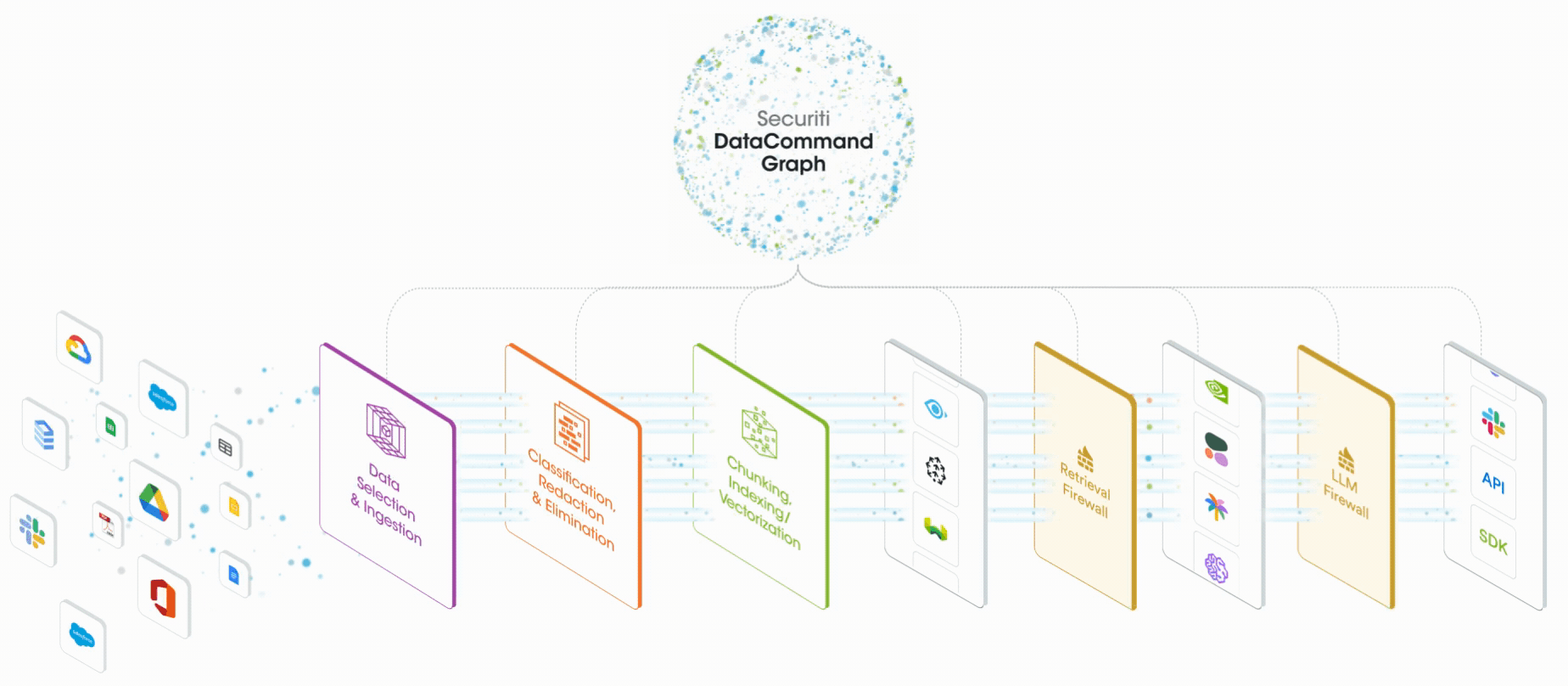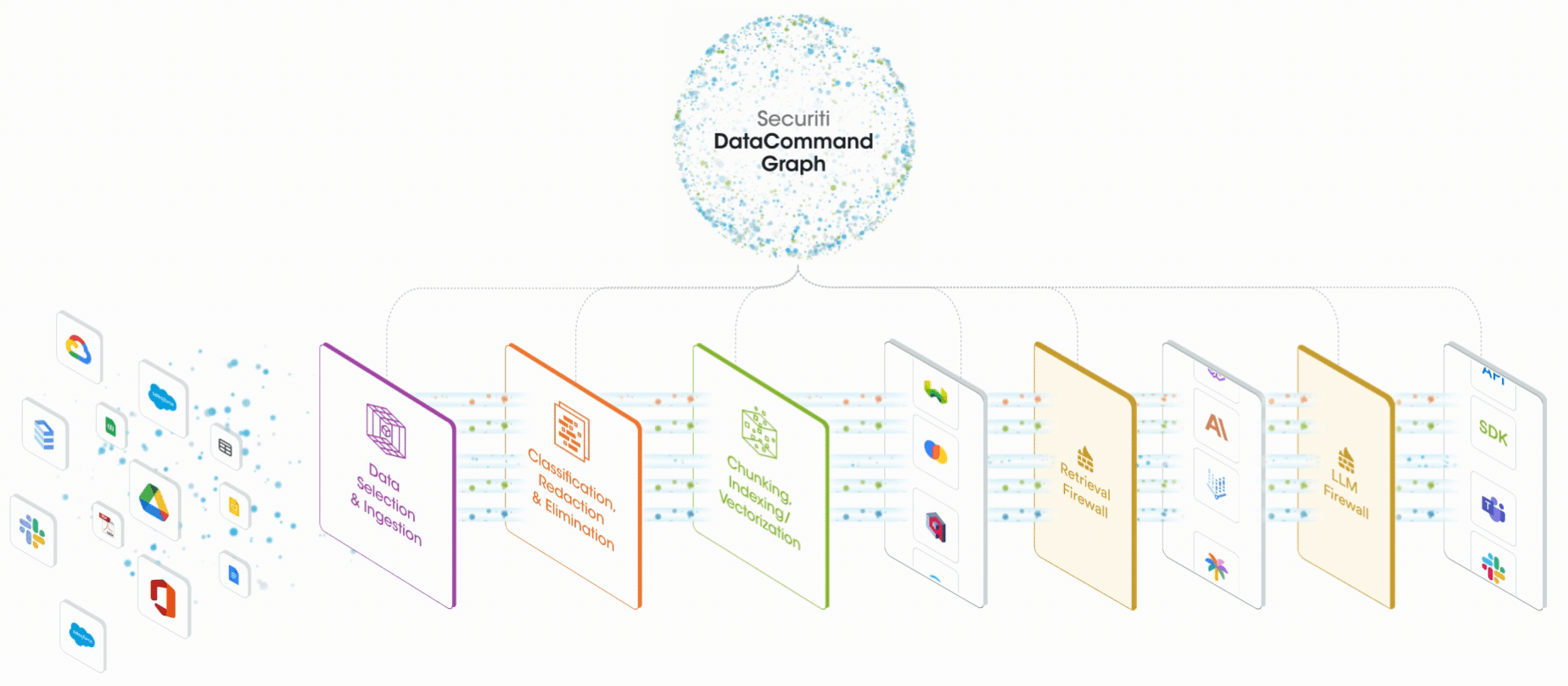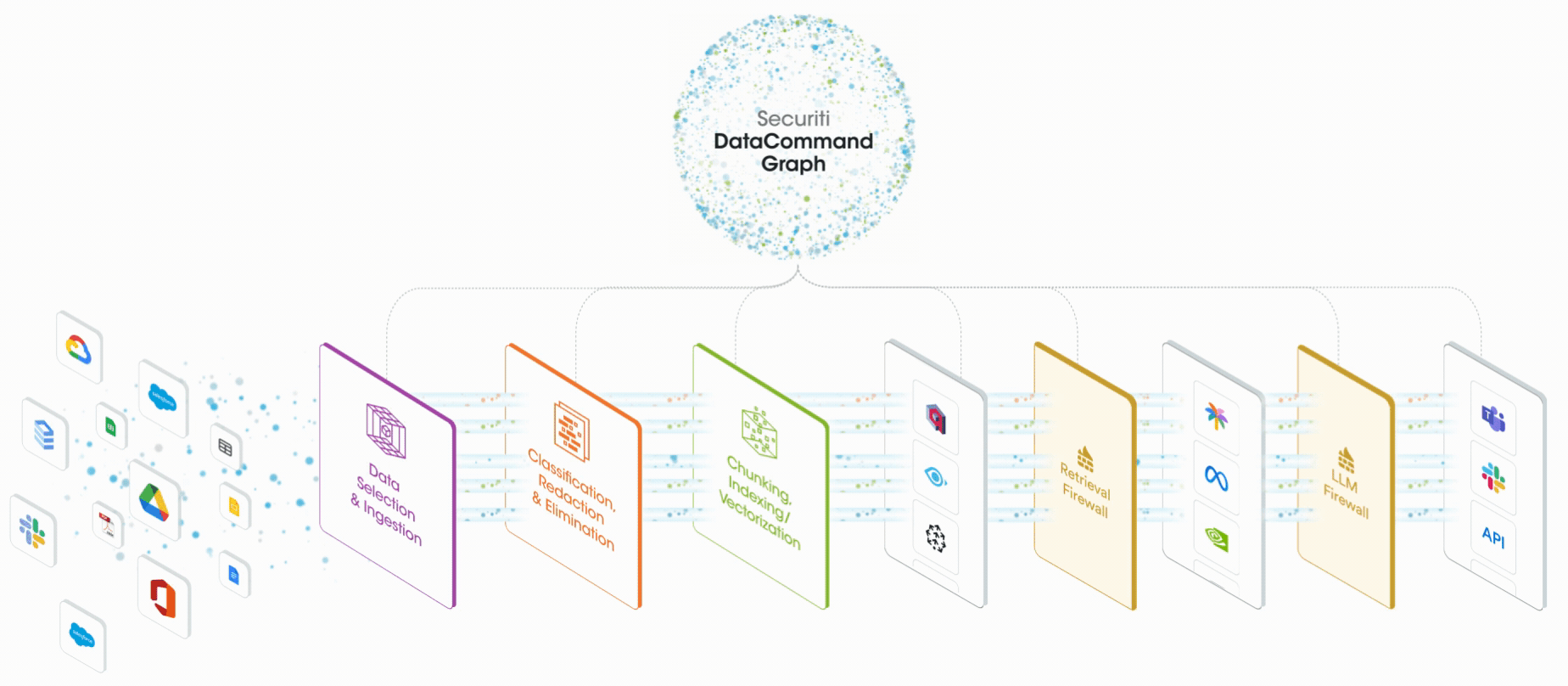
Securiti enables you to gain contextual insights for data with a multidimensional Data Command Graph that captures key metadata and relationships between them for all types of data. It provides a complete view of
- File categories
- Sensitive objects within a file
- File access and entitlements
- Internal policies and controls
- Applicable regulations for a file
- Lineage of files and embeddings used in GenAI pipelines
A key use case for lineage in GenAI involves ensuring that sensitive data is accessible only to authorized users. For instance, within an organization, the HR team may access employee personal data like salaries, whereas the marketing team cannot. If a marketing team member creates a prompt potentially accessing employee data, how can this be prevented? Securiti Data Command Graph monitors the data sources used by GenAI models for specific prompts and checks if the user has the right to access those sources. This capability helps identify and manage vulnerabilities that could expose sensitive data, using a clear visual map to establish appropriate controls.
5 Best Practices to Deliver Unstructured Data Lineage for GenAI
Here are five best practices to ensure your data lineage collection is accurate and efficient.
- Set your data lineage objectives to match your use cases: Data lineage collection is a resource-intensive process. To optimize resource use, ensure you collect the essential data lineage and not too much unnecessary information. Evaluate what lineage information your GenAI use case needs, and set your objectives.
- Choose the right data lineage tool: One of the challenges of unstructured data lineage is capturing the metadata, as it is often not fully defined. Selecting a tool that leverages AI and ML can significantly improve the ability to get complete metadata information as well as data transformations in real-time.
- Invest in a Data Command Center: The Data Command Center can break down silos to provide a unified view of your data landscape and capture lineage for both unstructured and structured data. It also addresses privacy, security, governance, and compliance across a broad range of use cases in your organization.
- Integrate with Data Quality and Security Initiatives: Use data lineage to support your Data Quality and Data Security efforts. Knowing where your data comes from, how it changes, and where it goes helps ensure its accuracy and reliability. This is especially crucial for sensitive information, which needs to be trusted and protected throughout its lifecycle.
- Promote a data governance culture: Foster a culture of Data Governance in your organization through training, awareness, and collaboration. This will ensure the value of data lineage is fully appreciated.
In Summary
Unstructured data, like emails, reports, and social media posts, is valuable but often underutilized due to its complexity. GenAI brings this data to the forefront, unlocking its potential for business growth and innovation. The success of GenAI depends on the safe and compliant use of unstructured data, making data lineage crucial to trace data movement across its GenAI lifecycle for integrity.
Securiti helps you overcome lineage challenges of data volumes and tool limitations, ensuring trust, transparency, and compliance in your GenAI projects. Learn to unlock the value of unstructured data safely and effectively. Download the white paper Harnessing Unstructured Data for GenAI: A Primer for CDOs.