Responding to Data Subject Access Requests
The following are the steps required to process and fulfill a DSAR:
-
Register, log and authenticate DSAR
Organizations must register data requests, log them in a system of record, and authenticate the user before starting work on their fulfillment, either manually or automatically.
-
Collect personal information
For organizations to prepare for DSARs, they will need to discover and categorize the personal data they process and store. This data is often stored on an array of systems within an organization and externally as well. The personal data must also be mapped to the individual owner of that data to facilitate the processing of DSARs. Leveraging a People Data Graph can help streamline this process. The collection of this data must also be done in a safe manner to avoid additional data sprawl which could result in greater liability.
-
Review and approve the information
After gathering the necessary information, organizations need to review the data and make sure it meets the DSAR requirements without disclosing proprietary information or the personal data of any other data subject.
-
Safely deliver customer information
The final response must then be delivered to the consumer securely. If a data breach or leakage occurs, it can cost as much as $750 per leaked record.
Here are several risks associated with fulfilling a data subject request you must watch out for:
- Requesters cannot be trusted without authentication.
- Managing deadlines is crucial to fulfilling DSARs.
- Data scanning should be automated, and done in a way that does not replicate copies of the data.
- Data processing should be centralized in a safe workplace to avoid personal data sprawl.
- Consumer responses should be encrypted to avoid data breaches.
- The activity must be tracked to keep a record for validating compliance.
- Data delivered to the wrong recipient can lead to significant liability.
One important factor to consider is that using traditional means will do more harm than good. For example, using emails to deal with DSARs can be dangerous as the risk of data sprawl increases when sending and receiving data over a system that is not secure. Moving personal information in an unencrypted system increases the risk of data breaches. It takes an average of 196 days for an organization to pick up on a data breach, making it essential for enterprises to fortify and automate their systems to protect themselves from any data breach.
How to Verify the Identity of the Person Submitting the Request?
For organizations, verification of a DSAR is a critical aspect of responding to and complying with such a request. A thorough and effective DSAR verification process is necessary to ensure the privacy, security, and integrity of personal data.
A typical DSAR verification process involves asking the individual making the request a set of questions and details to verify their identity. These can include government-issued identification that matches the details the individual provided as part of their request or a series of security questions.
While the timelines for such verification processes vary under different regulations, organizations are expected to carry out this process as soon as possible.
Who Responds to a DSAR?
If the organization has designated a data protection officer (DPO), they will often be in charge of fulfilling DSARs. If an organization does not have a DPO, the responsibility lies with a staff member knowledgeable in the domain of data protection and DSARs.
Time Limit to Respond to DSAR?
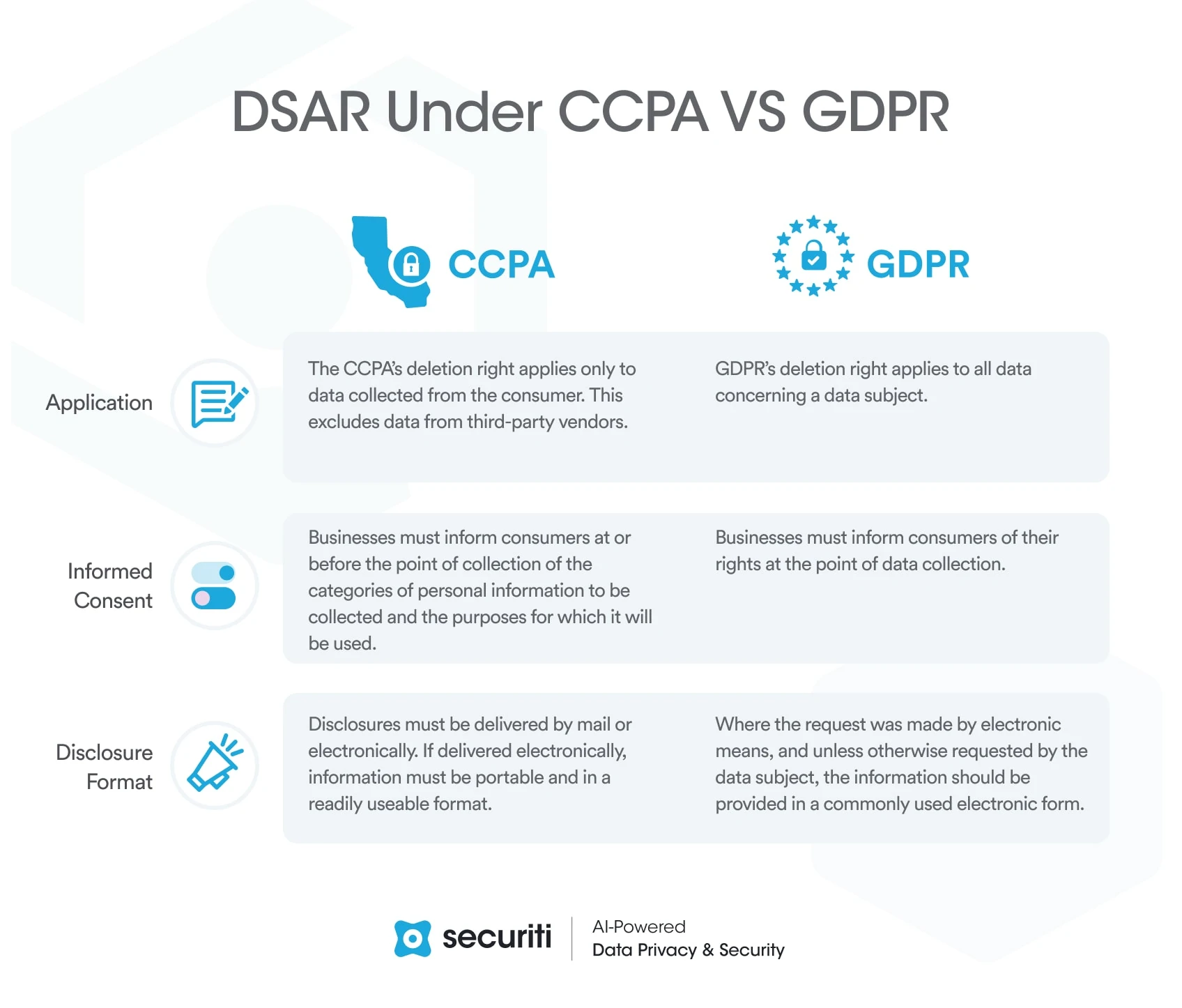
The exact time limit when responding to a DSAR will depend almost entirely on the regulation in question. For example, under the GDPR, organizations have a period of 30 days to respond with the possibility of a two month extension depending on various circumstances.
As explained earlier, each regulation has different provisions related to timelines to respond to DSARs. Therefore, organizations may find themselves having to tailor their compliance measures based on their relevant jurisdiction. However, a good rule of thumb is to ensure that such requests are honored as soon as possible.
Impact of Not Responding to DSAR on time?
Failure to respond to a DSAR carries significant implications for organizations as it opens them up to non-compliance risks under most data privacy regulations. The most immediate of these repercussions are the financial penalties an organization may face. Additionally, an organization may find its reputation severely compromised as well as diminishing trust among various stakeholders, especially the consumers.
Charging a Fee for the DSAR Response
In most cases, you are not allowed to charge a fee for handling a request. However, controllers are permitted to charge a fair price depending on administrative costs when a person requests more copies of their personal data being processed.
What Needs to be Included in a DSAR Response?
When responding to a DSAR, organizations are required to have the following heading in their response:
- A confirmation that the data subject’s personal data is processed.
- Access to the data subject’s personal information.
- State all the lawful basis for processing data.
- Mention the period, or criteria for which data will be stored.
- Any relevant information about how this data has been obtained.
- Any relevant information about automated decision-making and profiling.
- The names of any third parties information is shared with.
DSAR Response Challenges
While honoring DSAR requests is a significant regulatory obligation for most organizations, simply responding to such requests can pose a challenge in its own right. Depending on several factors such as volume of requests, data systems, ensuring data security and integrity, appropriate measures during data retrieval and other complications, organizations may find it challenging to coordinate various departments within the organization when responding to a single request.
These complications can get further exacerbated if third party information is involved, requiring compliance with several other regulations when handling such data. Hence, a well-defined and comprehensive approach is necessary when dealing with DSAR.
Refusing to Respond to a DSAR
According to ICO standards, a DSAR may be rejected if it is excessive or unwarranted. It's critical to keep in mind that each request's eligibility for an exemption must be considered individually. If you decline to fulfill a request, you must inform the relevant individual regarding the reasons for refusal and the available options which an individual has to file a complaint with the relevant authorities.