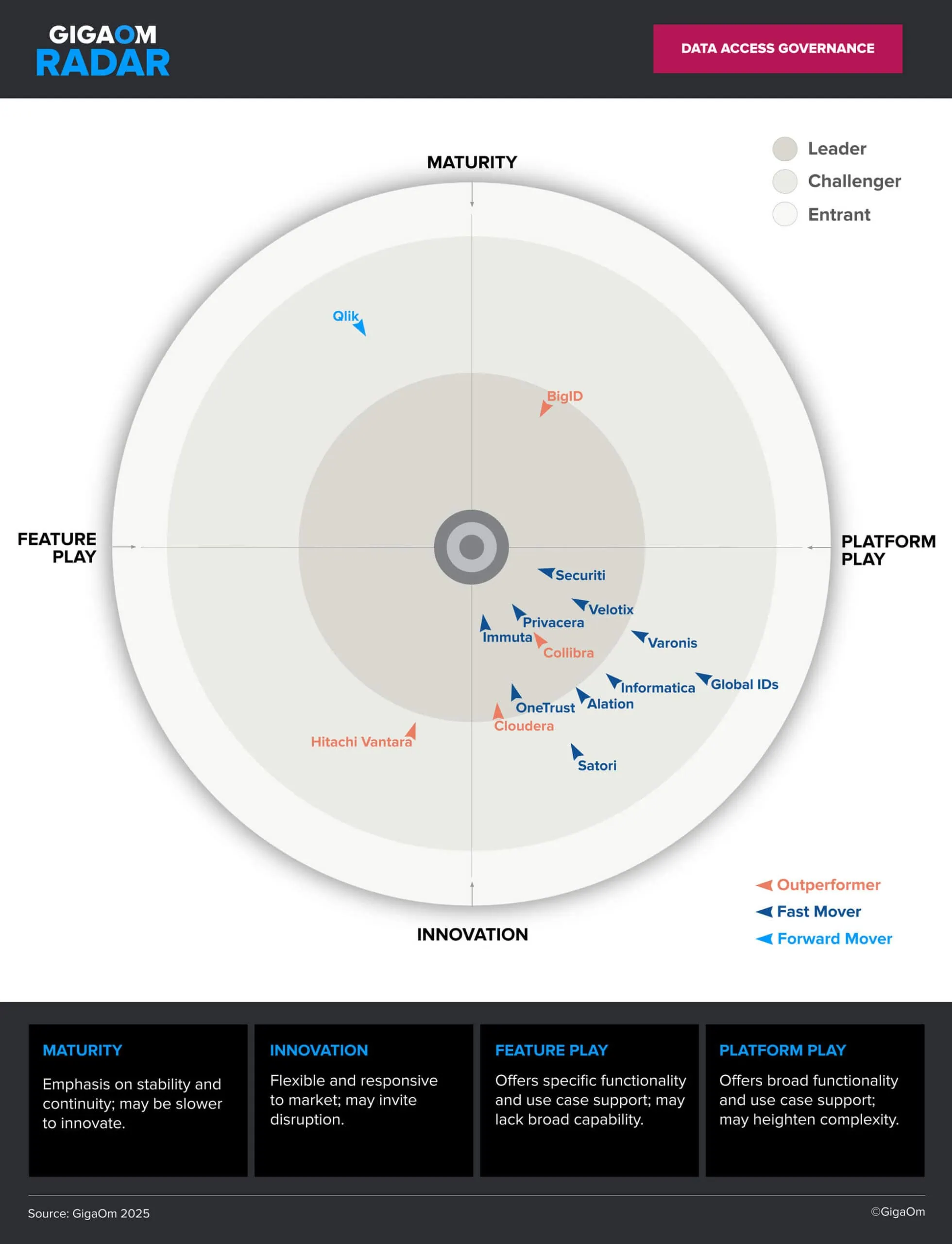
This recognition builds on Securiti’s recent top ranking in the GigaOm Radar for DSPM, further underscoring its continued innovation and leadership across critical areas of data security and governance.
Unified Data Access Governance Built for the AI Era
Securiti Data Command Center delivers a unified approach to data access governance, purpose-built for modern enterprises navigating the complexities of AI, data security, privacy, governance and compliance. The platform supports structured, unstructured, and streaming data across hybrid multicloud and SaaS environments, allowing organizations to consistently enforce access control policies across diverse data types and AI systems.
At the core of Securiti’s Data Access Governance solution, the Data Command Graph serves as a dynamic knowledge graph. Securiti uses native connectors to integrate with popular structured and unstructured data systems, automatically harvesting metadata and inferring contextual insights—such as data sensitivity, access entitlements, file attributes, AI model and agent usage, user access activity, and regulatory requirements. Built-in machine learning techniques and over 400 out-of-the-box classifiers enhance discovery, which organizations can extend and customize to meet their specific business needs.
The platform surfaces Data and AI Access Intelligence from the Data Command Graph via configurable dashboards. Securiti also provides integrated data lineage and lifecycle tracing, giving teams fine-grained visibility into how data is accessed, transformed, and shared. A built-in data catalog further enhances operational efficiency.
Securiti enforces access governance natively within key data systems using an attribute-based access control model. Security and governance teams can create and automate role-based policies using a no-code policy builder with dropdown-driven configurations. With support for dynamic data masking and context-aware row filtering, the platform enables organizations to apply least-privilege access at scale.
For AI systems, Securiti extends access governance to prompts and responses in GenAI pipelines. Securiti preserves access entitlement context from source data systems as they are used to build AI pipelines, and ensures responses delivered by the AI system are based solely on data to which the user has entitlement. The platform uses patent-pending LLM Firewalls to apply layered inspection and enforcement across the prompt, retrieval, and response stages of generative AI usage. Security teams can define policies that prevent unauthorized access or exfiltration of sensitive data by redacting outputs or restricting access..
By combining these capabilities, Securiti enables organizations to secure access not only to data itself, but also to the indirect ways data is used in AI applications, ensuring that sensitive enterprise information remains protected across today’s dynamic, distributed environments.
Securiti Earns Top Ratings In Key Technical Features and Business Criteria
Thanks to its unified platform-based approach to data and AI access governance, the GigaOm report recognizes Securiti for excellence across several technical and business dimensions:
Key & Emerging Features
- Unified View: Insights into where data resides, who is requesting access, whether access has been granted, and how the data is being used.
- Generative AI Governance: Ability to secure data access, privacy, and regulatory compliance for GenAI use cases.
- Real-Time Risk & Vulnerability Assessment: Continuous assessment of data security and risk posture across hybrid multiclouds.
Business Criteria
- Ecosystem Integration: Integration with a wide variety of structured and unstructured data systems.
- Speed of Data Access: Ability to accelerate governed, secure access to enterprise data assets.
- Intelligent Customization: Understand user preferences, behavior patterns, and improve efficiency through automation.
- Change Resiliency: Sustain governance as unstructured data, GenAI models, and data protection risks proliferate.
Enabling a Modern Data+AI Security Fabric
“Securiti was founded on the belief that modern enterprises need a unified platform to secure and govern data across hybrid multicloud environments and enable safe AI adoption,” said Rehan Jalil, CEO of Securiti. “This recognition in Data Access Governance by GigaOm, following our DSPM leadership, further validates our mission to deliver a scalable, intelligent, and integrated platform for data+AI security, privacy, governance, and compliance.”
The 2025 GigaOm Radar for Data Access Governance provides an independent assessment of leading vendors across technical and business criteria. Securiti’s leadership position in both DAG and DSPM categories reflects its ability to deliver comprehensive data security and governance outcomes at enterprise scale.
To learn more, explore a range of resources below:
About Securiti
Securiti is the pioneer of the Data Command Center, a centralized platform that enables the safe use of data+AI. It provides unified data intelligence, controls and orchestration across hybrid multicloud environments. Large global enterprises rely on Securiti's Data Command Center for data security, privacy, governance, and compliance. Securiti has been recognized with numerous industry and analyst awards, including “Highest Rated DSPM Leader” by GigaOm, “Customers’ Choice for DSPM” by Gartner Peer Insights, "Cool Vendor in Data Security" by Gartner, “AI Governance Leader” by GigaOm, "Privacy Management Wave Leader" by Forrester, “Worldwide Leader in Data Privacy Compliance” by IDC, "Most Innovative Startup" by RSA, "Top 25 Machine Learning Startups" by Forbes, and "Most Innovative AI Companies" by CB Insights. For more information, please visit securiti.ai or follow us on LinkedIn or X.
Media Contact
Alex Daigle
Securiti@OffleashPR.com