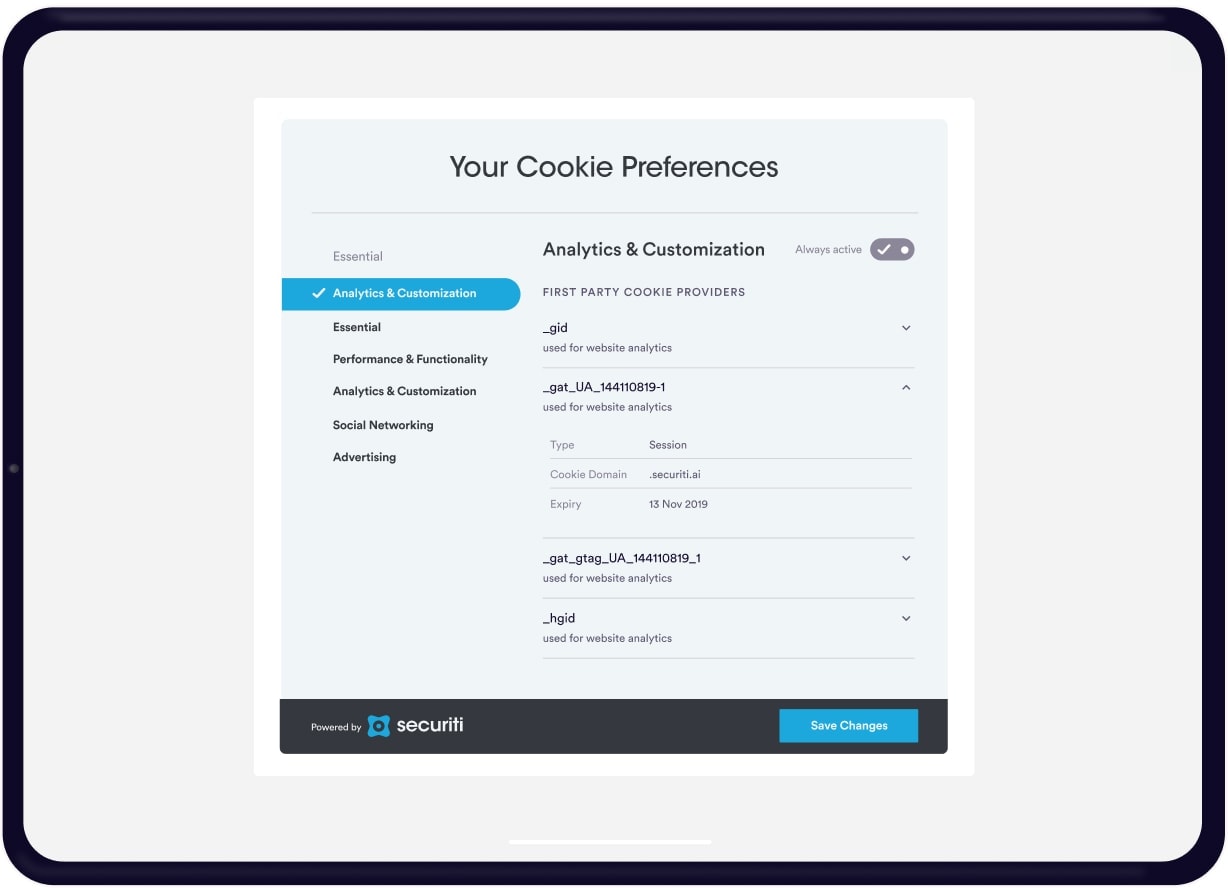
The processing of personal data for direct marketing purposes is allowed under the strict condition that the data subject has given prior consent. Direct marketing may include the processing of data in order to promote goods, works, services on the market by making direct contacts with a potential consumer using communication means, as well as for the purposes of political campaigning.
A data subject has the right to request an operator to cease sending them promotions of this sort, and the operator must comply with such a request immediately.