1. Discover Data Assets
Data asset discovery is critical to ensure the identification and inventory of all the data systems across the organization’s data environment. DSPM solutions provide a comprehensive data asset discovery engine. It enables teams to sift through their entire cloud environment to identify and catalog data assets properly.
For instance, the solution can efficiently identify shadow data assets, such as unmanaged databases that are running on top of compute instances. Similarly, it can further look for dark data assets, which are forgotten data stores, i.e., unknown to the IT teams.
2. Classify Sensitive Data
To safeguard data adequately, it is imperative to gain complete visibility into what data is sensitive, where it is located, and whether it needs additional security measures. DSPM solutions can help organizations achieve that visibility through effective data classification.
By leveraging machine learning (ML) and natural language processing (NLP) techniques, DSPM can discover data and classify it according to its respective sensitivity level. Amongst the many key aspects, DSPM can help identify various data elements across different data formats.
Organizations can also choose to create customized classification policies, which are tailored to their needs or risk appetite. With actionable context around their data, such as privacy or security metadata and regulatory requirements, organizations can effectively address data obligations.
In the cloud security sphere, it is common knowledge that misconfigured data assets can lead to security threats. In fact, surveys reveal that misconfigurations are among the leading cause of cloud data breaches. Hence, resolving configuration errors is paramount to maintaining a robust data secure posture.
By combining data classification capabilities and data security posture rules, DPSM solutions can assist organizations in resolving misconfigured data assets. DSPM solutions help organizations narrow their focus down to only data assets that contain sensitive data. This further enables security teams to prioritize misconfiguration risk and avoid false positive alerts.Organizations can resolve misconfiguration issues by alerting data owners or through auto-remediation of security violations. Teams must continuously assess data system configurations for errors and harden their configuration guidelines by integrating industry best practices and standards.
4. Prevent Unauthorized Data Access
Preventing data leaks and unauthorized access requires insights into data type, users, roles, access entitlements, locations, and activity. Using those insights, access governance teams can fortify access to their most important data, sensitive data.
DSPM solutions leverage access intelligence and governance to deliver much-needed insights, enabling secure data access policies. The solution delivers comprehensive insight into sensitive data along with details about data users, permissions, roles, and access usage. This helps organizations harden access permissions and policies, limiting access to only authorized users and to only the needed data.
A more robust DSPM solution may further allow organizations to combine access and regulatory intelligence, ensuring data transfers follow cross-border transfer rules. DSPM solutions further foster the principle of least-privilege access by isolating inactive and overprivileged users.
5. Secure Data Lifecycle
Data transmits continuously from systems to systems or applications in streaming environments. This continuous data transmission flow at scale creates various security posture management challenges and risks for organizations. For instance, hundreds of sensitive data in streaming Topics can be transmitted to unauthorized consumers if not classified and governed.
DSPM solutions help organizations trace data processing activities via data mapping and understand data lineage. Data teams can analyze the lineage to grasp how the data moved from different systems, duplicated, changed, or transformed over time. By using such valuable insights, organizations can determine whether security, privacy, and access governance controls are consistent throughout streaming environments.
Thinking Beyond DSPM, CISOs Should Cast a Wider Net
At an enterprise level, DSPM is the tip of the iceberg. While DSPM is crucial in protecting data everywhere across an organization’s environment, organizations that are truly committed to fortifying their cybersecurity must adopt a wider and more progressive approach. To cast a wider cybersecurity net, CISOs must consider the following:
1. Reduce Redundant, Obsolete & Trivial (ROT) Data
Redundant, obsolete, and trivial (ROT) data is any piece of information that a business may continue to retain after that particular data has either served its purpose or has no operational value. Accumulation of ROT data carries a significant amount of risks. For instance, if the ROT data contains sensitive information while it lacks proper security controls, it may pose serious security risks. Compliance may be at risk if the data is retained beyond its regulatory requirements. Similarly, an organization’s operational value and data management may get compromised if it keeps accumulating large volumes of data.
CISOs must discover and reduce ROT data to minimize the attack surface. DSPM can play a critical role in helping discover redundant, obsolete, and trivial data across an organization’s data landscape. Upon detection, organizations can minimize the ROT data via remediation measures like data deletion or delegation to someone who can better decide if the data needs to be deleted or not. Teams may also quarantine the data until a data steward decides on further remediation measures.
2. Enable AI Security & Governance
Generative AI (GenAI) has demonstrated remarkable capabilities in the past recent years. Not only has it transformed organizations significantly, but also managed to make itself a necessity. However, this transformative technology comes with a number of potential risks and challenges. For instance, more and more countries are coming up with AI regulations to ensure the responsible development of AI technologies. Keeping up with the growing number of global AI regulations is a necessary step, yet a complex web to navigate. Similarly, AI has brought with it a number of unprecedented risks that have never been heard of before, such as AI poisoning, AI prompt injection, and AI model theft, to name a few.
CISOs must strive to build a robust AI security and governance framework to establish proper controls and enable the safe adoption of AI technologies. CISOs may begin by creating awareness around LLMs’ functions, behavior, weaknesses and strengths, and potential risks. Detailed policies should further be created to promote awareness and minimize the use of unsanctioned AI across the organization. Established frameworks like Garnter’s AI Trust, Risk, and Security Management (AI TRiSM) framework must be leveraged while developing new AI applications.
3. Manage Data Privacy
Honoring people’s data privacy rights requires complete insights into personal and sensitive data along with individual identities. However, due to data proliferation, data is now scattered across different systems and geographies. This makes it difficult for data teams to map every data element to global overlapping regulations or assess privacy risks.
Some advanced DSPM solutions help streamline full-lifecycle data privacy operations. By leveraging contextual data, AI intelligence, and automated controls, organizations can simplify their privacy risk assessments, data subject rights management, consent management, privacy notice management, and global compliance.
4. Analyze Breach Impact & Automate Notifications
Efficient data breach impact and response management is critical in the event of cyber incidents, such as a data breach or violation. In the absence of such a critical system, an organization may face legal penalties, financial losses, and a damaged reputation. It is imperative that organizations handle breaches as soon as they become aware of the incident and respond efficiently, especially when it comes to breach notifications.
How Securiti DSPM Can Help
According to Gartner’s Hype Cycle™ report, data security posture management is still in its embryonic or transformational phase. Hence, its potential is yet to be fully explored, and some added capabilities are to be expected.
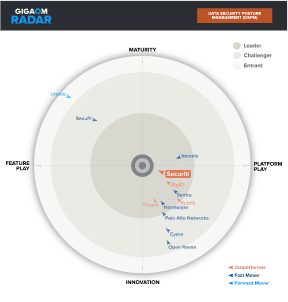
Rated #1 by GigaOm Radar and Gartner Customer Choice, Securiti DSPM solution, built-in to a broader Data+AI Command Center, enables organizations to secure their data and AI everywhere.
Organizations can leverage Securiti DSPM to:
- Discover cloud-native, shadow, and dark data assets via 200+ connectors and APIs.
- Accurately classify data with increased efficiency and at scale.
- Go beyond traditional classification with granular data labeling, tagging, and metadata enrichment.
- Provide insights into ROT data with the option to mitigate it via Deletion, Delegation, or Quarantine measures.
- Use 700+ pre-defined rules to identify and resolve misconfigurations.
- Enforce least-privileged access controls, fostering a zero-trust data security model.
- Dynamically mask sensitive data across large-scale deployments.
- Automate data privacy operations.
- Secure the complete lifecycle of data, including data in motion.
- Get full transparency into AI systems, risks, processing activities, and AI regulatory compliance.
- Streamline breach notifications with automated DSR.
- Easily extend DSPM to unify data security, privacy, compliance, and governance controls using a single platform.
Interested in learning more? Request a Demo now.