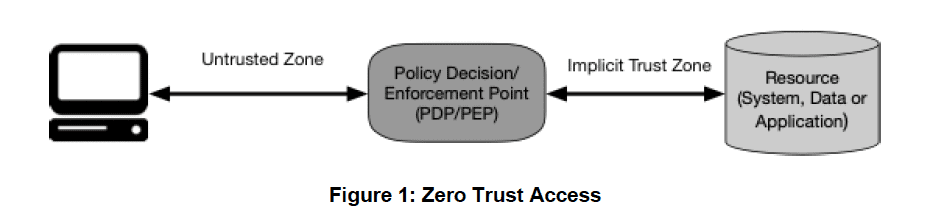
Source: NIST SP 800-207, Zero Trust Architecture3
When securing access to data, the trust algorithm needs data context such as sensitivity, applicable security and privacy laws, consent, behavior, and location in addition to knowing who is requesting access as inputs to decide how the request should be processed.
Think about the airport analogy again. Airports do a great job of implementing least-privilege security to ensure access to sensitive airport infrastructure is limited to people who absolutely need it to perform critical operations. For instance, access to the following airport resources is restricted in many ways -
- Cockpit: Pilots, cabin crew, and technical staff
- Airplane seats: Passengers based on ticket class
- Baggage: Logistics and customs staff
- Food: Hospitality teams and cabin crew
- Inflight communication: Pilots and cabin crew
Note that access to the aircraft is not a simple yes or no decision. All subjects including pilots, cabin crew, and passengers need aircraft access. However, the airline has to ensure that passengers do not enter the cockpit. This is an example of managing partial access. Similarly, in the digital world, granting data access is not always a black-and-white decision. Sometimes, an analyst needs access to a data set or a file containing sensitive information such as customer PII or financial records to perform a critical analysis. Rather than block access and hurt business, intelligent controls should be applied to allow access while masking sensitive data elements based on security or privacy context.
“Implementing Zero Trust security to protect data requires organizations to complement IAM and network security tools with solutions that can provide intelligent data context and orchestrate partial access across structured and unstructured data objects at scale.”
Operationalizing Zero Trust Data Security With Least Privilege Access
Implementing Zero Trust security to protect data requires organizations to complement IAM and network security tools with solutions that provide intelligent data context and orchestrate partial access across structured and unstructured data objects at scale. Let’s examine the steps an organization needs to follow to improve Zero Trust data security.
- Discover All Data Systems: An organization needs to automate the discovery of different structured and unstructured data objects across public clouds, private clouds, SaaS applications, and data streams. The discovery process should ensure visibility into non-cloud-native, dark data assets unknown to IT teams.
- Gain Sensitive Data Intelligence: The next step is to accurately classify, label, and tag sensitive data elements in each data store. It's important to identify personal data belonging to individuals, as protecting such data is required by regulation and is the foundation of trust between an organization and its customers.
- Identify Sensitive Data Obligations: Data, especially sensitive data, has many obligations as an organization must comply with various data security and privacy laws and internal governance controls. Proactively identifying these obligations is critical to ensure that organizations deny access requests that violate these data obligations.
- Segment Identities by Roles and Permissions: An organization needs to identify identities that need data access and segment them by roles. This mapping can be informed based on current access activity and should limit permissions to what is needed to perform critical business functions.
- Govern Data Access With Granular Controls: The next step is to orchestrate data access controls, blocking unauthorized requests and granting authorized access while masking sensitive data elements based on tags at scale.
- Remediate Data Security Posture Risks: Organizations must assess the data security posture to identify vulnerable systems, especially misconfigured assets containing sensitive data. Access to such systems should be denied and carefully monitored until vulnerabilities have been addressed.
By governing data access dynamically per request and granularly at a data element level, organizations can add a layer of defense to improve Zero Trust data security.
Why Zero Trust Data Security Matters
Data-driven technologies and decision making offers incredible economic opportunities to businesses and conveniences to consumers. However, absence of intelligent Zero Trust data access controls can leave an organization holding the data in a difficult position. Overly strict controls impede innovation by locking down data access whereas loose controls increase the risk of data breaches and consumer privacy violations. Finding the right balance is essential.
The National Cybersecurity Strategy supports increasing legislation around data protection, especially PII data. When implemented effectively, Zero Trust data security enables organizations to harness data by sharing it with internal and external teams while maintaining strictest security controls and honoring the privacy rights of consumers. Zero Trust security can help an organization innovate using data while strengthening consumer trust and competitive differentiation in a digital world.
Managing Response When Zero Trust Fails
No Zero Trust implementation can completely eliminate risk. In Zero Trust, not only should an organization assume an attack but also prepare to handle one. The key step when a breach is suspected is to validate and contain the incident by identifying the affected data assets, the root cause, and remediation measures. Once the breach is confirmed, it's essential to identify the impacted data elements, consumers, and regulatory laws to assess the damage caused.
Accurate and automated impact assessment is critical as it enables the organization to better coordinate with investigating and regulatory authorities, share threat intelligence, and accelerate victim notification. All of these aspects of breach management get significant importance in the National Cybersecurity strategy.
When all eyes are on one company, breach response is more than a regulatory obligation. How an organization mitigates risk and communicates with stakeholders sets the tone for incident recovery and has a long-term impact on its brand reputation.
How Securiti Strengthens Zero Trust Data Security
Securiti can be a critical cog in your Zero Trust security architecture, complementing IAM and network security security solutions with intelligent sensitive data context and automated controls. Security helps organizations to unleash the power of its data and implement a non-disruptive approach to Zero Trust with frictionless data security, privacy, and governance controls.
With Securiti's Data Controls Cloud, an organization can -
- Discover structured & unstructured data across clouds, SaaS, and streaming platforms
- Accurately identify predefined and business-specific sensitive data elements
- Monitor data access activity and eliminate over-privileged roles
- Dynamically mask sensitive data at-rest and in-motion
- Prioritize and remediate risky misconfigurations of sensitive data objects
- Securely share data in compliance with global security and privacy regulations
- Proactively plan and automate data breach lifecycle management
Access our Data Access Intelligence & Governance Guide to learn how your organization can operationalize Zero Trust Data Security with granular access controls.
References:
- FACT SHEET: Biden-Harris Administration Announces National Cybersecurity Strategy, The White House
- Zero Trust Slow to Build Momentum, 2022 CyberRisk Alliance Research Study
- NIST Special Publication 800-207, Zero Trust Architecture